Aug
|
A Test Post 2023 |
Feb
|
Running Code on a Self-Contained Timer
2020
[Note: Updated A year without a post? Hrm. There is a post dated 2019 but it's in the So here's a little post on running code on a timer; I don't know if C# can do this more elegantly, but I don't think VB can. Hence: this. There have been far too many times I've wanted to run code that only displays something for a couple of seconds and then hides it. While simple enough, I really don't want to have to create a Timer component, instantiate it, run the code, and then tear it all down again. Just display a thing and then go away - that's all I want! I couldn't even have a half-solution by instantiating and executing the Timer without having an explicit method for the Timer to call into when the time elapses, such as [note that all code formatting in this post is wonky; a lot of it isn't really fixable]: I may make a specific extension method for this sort of thing but that's only tangibly why we're here and so will have to wait for another time. So, today, I decided to try and get this sorted out. While it would probably have to be a Task, I wasn't entirely sure the best way of going about achomlishing accomplishing this and so I began; after various experiments, here's the result. And the enumeration: The formatting is completely off in this post, so it doesn't look like that in actuality. I also have extension methods for certain things (eg. ensuring a value is appropriately clamped between a range) but I've replaced them with "pure code" versions above. The above allows you to run code after a specific duration has elapsed, and optionally run additional code based on an event that occurs - all without having to create a separate Timer control that needs to be manually instantiated, hooked, and torn down. Again, this appears to be true for VB. While not posted here, I have another version that uses a TimeSpan instead of a duration (meh; not a major thing) as it's "more appropriate", and a version that has the initial
Oh, an example? Right - yep, this is the basic version that only specifies the code that should be run after a duration has elapsed. This hides the (eg.) ToolStripLabel Verified OK! indicator after two seconds and is used to let the user know a thing they validated/verified/whatever is fine. And another version that does the same as the above but also adds code that hides the visual indicator if the user clicks on it (this is a simplified version of code being used in Twitter Delitter). And that's about it. While countless changes could be made, it would make this post unwieldy; I have a particular loathing for code examples that have extraneous fluff that does nothing but obfuscates what is being shown. Use this code at your own risk, etc - I (mainly) use VB .NET so you probably shouldn't listen to me in the first place... |
Mar
|
Installing Java on Windows XP
2018
This blog seems to be turning into a problem-solving database thingy. Still, it's better than it getting no updates at all, right? This particular post is about trying to install horrible Java on horrible Windows XP. Namely - you can't. Or, at least, I couldn't. Double-clicking on the Java installer (either the online or offline versions; doesn't matter) results in a flurry of disk activity and then a whole lotta nothing. Looking in the system's
According to some of the stuff I read, the version of the installer those Oracle/Sun idiots use doesn't run on Windows XP despite them telling you it, uh, does. The Java runtime might, but the installer used to install it... doesn't. It doesn't surprise me that Java is as cack as it is. Grab an earlier version of the Java runtime and install that, instead. Here's the one I used (note the installer is still signed by Oracle - important!): View Page: Java Runtime Environment 8.0 build 152 Why not use an older one directly from Oracle themselves? Because those morons want you to create an account to just download it! Hahaha-ha-ha... ha. No. When running the older installer, ignore the warning that says it may not work in Windows XP - it's just saying that because even Oracle knows Windows XP is a huge, outdated crock of plop. I'm running Windows XP in a virtual machine to run a Java JAR file, otherwise, I have no use for Windows XP nor Java. I'm glad Java is practically dead. And Windows XP. |
Nov
|
Windows 10 Start Menu not Working?
2017
This problem is extremely annoying: sometimes, the Start menu in Windows 10 will outright stop working. It won't appear when the Start button is clicked or the Windows Key is pressed. In addition, various Windows 10-style windows (such as the system's volume control that appears in the top-left of the screen when the volume is changed) will also not appear. Right-clicking on the Start button will then cause any 10-style windows to then draw... it's all very weird. After many months, it seems I may have stumbled upon a fix for the issue. Every time I tried restarting or shutting down the system, Windows always complained about there being a task that wouldn't exit. The string given is:
Microsoft introduced a "feature" that allows Windows to finish installing device drivers after an update or restart. Awesomely - it doesn't work. This broken feature has been the cause of months of (random) frustration and re-installations. Anyway - whatever, onto the fix. Hopefully it's the fix; I haven't ran into the Start issue since.
To do this using the Start menu (eg. you're performing this as a preventative measure), just type If you have a broken Start menu, you can either click on this link right here or press Windows Key+R to open the Run window and then type the following, followed by pressing the Enter key.
Include the trailing colon character otherwise you'll get an error.
That should be it. |
Oct
|
Accounts Site Revisit
2017
No updates for nearly two months? Like I mentioned before, that's mainly because I can't really think of anything to post. But, today, I am posting. Accounts! If you're a registered user of my software, then expect to see an update of the Accounts site in the near future. I've just upgraded all of the backend libraries and such, and the (local development) site is completely broken. It appears things changed in Laravel, Apache, and PHP - so that shizz got busted. I had to struggle with working out why Apache kept giving me 404 errors in regards to virtual hosts. Here's what I finally came up with that seems to work in Apache 2.4.x. Just that took a few hours (as I followed numerous false trails), but it's done now and I can just apply it to all of my other virtual hosts. Next-up is fixing the Laravel errors, which in all honesty, don't really make much sense. Thankfully the Still no idea what the problem is, though. |
Sep
|
Hot Electrolytes Drink
2017
Here's a little electrolytes drink I've come up with to supplement sodium, potassium, and any other essential nutrients/chemicals that you may have the ingredients laying around for. I won't get into the specifics of why I'm making or having this drink other than to mention the following for search engine purposes: zero carb, low carb, keto, ketogenic, LCHF. The listed eating regimes are diuretic in nature, so extra supplementation is required; the consumption of incidental salts is very low due to not eating processed foods. In fact, adults should aim for 5g - 6g of sodium chloride per day (table salt is only 50% chloride). Research is out there, if you're interested. This recipe - if you want to even call it a recipe - isn't zero carbohydrates. It's extremely low, but it's not outright zero. You can make substitutions to remove the (already low) count if you prefer, by, say, substituting the cube for bone broth. Ingredients
PreperationCrumble the bouillon cube into a cup and fill it up with hot water. Add in a small-ish quantity of the rest of the ingredients, mix, and taste. If you can handle more of the salts, add more of them in. Mix, again, and taste. Keep doing this until you determine how much of the ingredients you can have without it being too salty. The aim is to get as many of the electrolytes in as possible while keeping it palatable. The more there is, the better. I use vinegar and Worcestershire sauce to give it a much stronger flavour; I love acidity, so both of these work brilliantly. I specifically chose Henderson's Relish as its carb count (7g per 100g/ml) is much lower than, say, Lea and Perrins which is way higher at 21g. Sainsbury's own brand is 30g! Hell naw, son. You can add calcium and such, but they float in the liquid and so aren't fun to consume. Horrible and bitter; better off taking it in tablet form if you require supplementation. Don't forget: If you're doing zero or low carb, or ketogenic, your mineral and vitamin requirements are greatly reduced. No competing with glucose for cellular uptake or any of that crap. Do note that vegetables will interfere with absorption, so zero carb has even lower requirements than the other LCHF diets.
|
Sep
|
Sucralose
2017
Still can't think of much to post about, but checking out the viewer stats shows that there really isn't much point. The visitor count tanked years ago when I neglected the site. Anyway, today I'm going to post about the Sucralose sweetener as it may save people a lot of money. Alright, a bit of background: I do zero carb. Originally I did a ketogenic (keto) diet but that shizz ain't good enough for a guy like me, so I now almost (almost!) exclusively eat meat and cheese. I don't need to be that strict - but I am. I plan on bodybuilding after this massive cut I'm through so I need to get this right. I use sweeteners quite a lot and so I've been buying Stevia / Sucralose / Erythritol / Saccharin (delete as applicable). Except, the other day I got annoyed with how much Stevia sweetener I had to use as compared to previously. Then, somehow, I stumbled upon 100% pure Sucralose. This is what manufacturers dilute (typically along with a sugar - which is idiotic considering the point of sweeteners in the first place!) to create the final product. 100% pure Sucralose is 600 times sweeter than sugar. It is completely insane how potent the stuff is when it hasn't been diluted down to near-uselessness (hello, homoeopathy!). I put literally 30 milligrams in a cup of tea; this pure powder here is a 100g pack. I bought two packs. I'll still have a lot left over after the heat death of the universe... [No: sweeteners aren't bad for you, you colossal idiot] |
Sep
|
A Bit Quiet...
2017
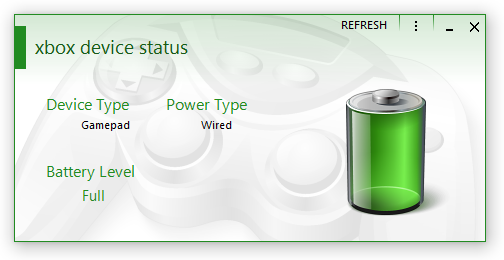
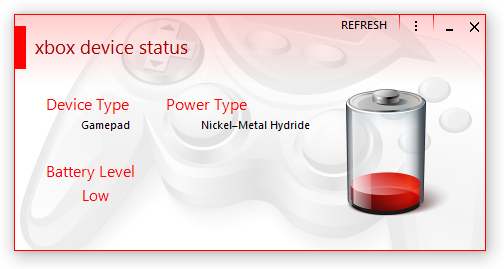
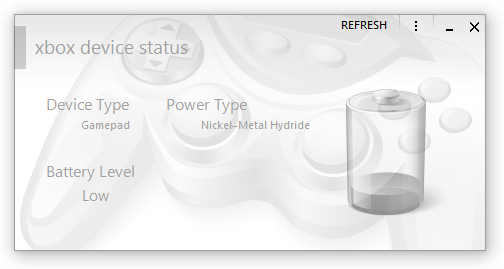
I haven't gotten lazy in writing new blog posts, it's just I honestly don't know what to write about. I've done a lot of work on XBox Device Status, but not really anything I'd consider interesting. Hmm, actually - it could be interesting to a few people as I'm doing work with XInput and getting battery and state information. Someone might be interested in doing that from within C# / VB .NET? I'm also considering doing a one-week fast that I could write about. Who knows. Maybe I should resume work on that Assembler thing I started a while back? It's just the tedious parsing that's doing my head in and putting me off. |
Aug
|
XBox Device Status 1.00
2017
A new project is out: XBox Device Status. For some reason, Microsoft haven't provided a way to display the battery levels of any connected Xbox pads on Windows PCs. There is a Windows Store app specifically for configuring the Xbox Elite Controller (US version here) that sort of shows it, but it's horrendous and not really designed for that. In steps XBox Device Status. It's an application (by me, of course) specifically designed for showing the battery levels of any attached Xbox pads and headsets. Version 1.01 will add support for events. There was quite a delay in releasing XBDS as I ended-up making numerous changes to my Metro library, changing existing controls and adding a new one. This library is why XBDS looks the way it does; it's my implementation of how Metro should've looked before even Microsoft themselves released their original version all those years ago. A form with large empty areas with a mid-grey background is just terrible, regardless of what idiocy you use to try and justify the design decision.
The Free Edition does what most people want, showing the battery level of a connected controller. The Home/Enterprise Edition provides extra features such as headset levels, system tray support, and the aforementioned events. More Home/Enterprise features will be continually added. Additional screenshots are available here. |
Aug
|
Spurious/Incorrect .NET Form.Activated() Event
2017
Notice: Using the "fix" below can result in the form's Notice 2: I've added another version below. A couple of new categories for this blog: But, let's continue with the subject of this post: the Quite a few years ago I created my own Metro-style form based on the idea of Microsoft's flat-style interface. Metro was approximately a couple of years away from release and there wasn't really any screenshots of what it would look like. I ploughed on with my version - including a break of a year because it took a long time to get it working correctly as working with forms that have their The biggest issue was getting Windows to treat the borderless form as a true window; it just didn't give a crap about it. A quick way to tell if Windows regards a form as a true window is to minimise it to the taskbar. Does it immediately disappear from view? It's not a true window. Does it animate down into the taskbar? It's a true window. There were two issues remaining (that I remember, anyway): restoring the window from its minimised state causes the window to gain an extra X number of pixels on its height. That's still an issue and seems random as to which form it affects. The fix I put in-place seems to work most of the time, but regardless, the child controls gain extra height with/without the form growing in size. Clearly more work to be done, there. The second issue which I'm going to talk about here is the form's It seems somewhat random when it happens, but here's how it generally goes:
This causes a problem in my particular case because I handle and expose the activation event via a For example, here's a (currently work-in-progress) form that's active:
And here's that same form when it has become inactive:
As you can see, having the form become active when it actually isn't is confusing to the user. And extremely irritating to me. My first quick go at fixing this seems to work; I'll have to keep testing it over the long term but it seems like it may have solved it. Not a fan that I have to do this in the first place, but what can ya do? Have this at the first line(s) within the Here's another version (see notice at top of this post):
It appears I'm not sure if it's worth putting a check into the |